CarSaver: A complete one-stop solution for all your car buying requirements
Category: Automobile/SaaS
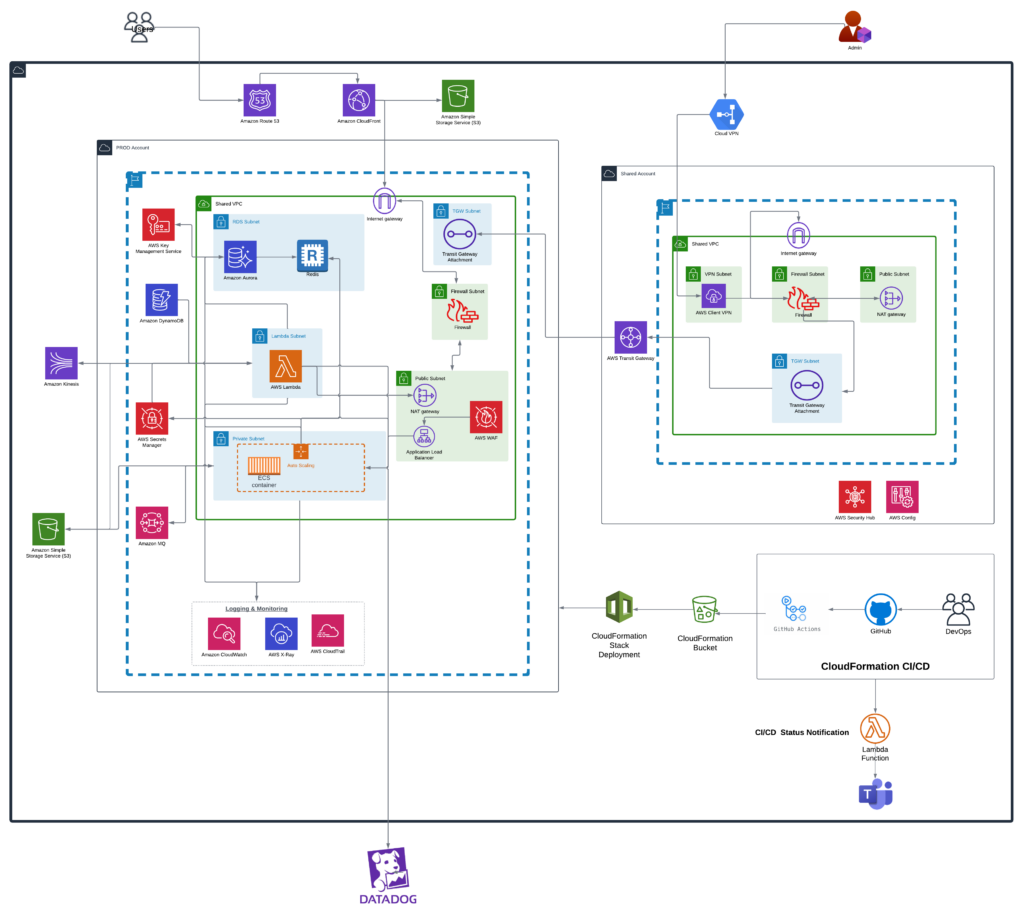
Services: Managed Engineering Teams, AWS managed service Config, DevOps,Cloud Architecture Design, and review, Policy and Compliance Management, Security Auditing and Threat Detection, Configuration Remediation, Change Management and Tracking